X.509 is a widely used standard for defining the format and structure of digital certificates, which are used in authentication services to establish the identity of entities in a networked environment. X.509 defines the syntax for certificates and the protocols for certificate management and authentication. Here are the key components and services related to X.509 authentication:
- X.509 Certificate: An X.509 certificate is a digital document that binds a public key to an entity, such as an individual, organization, or device. It contains information such as the entity’s name, public key, issuer, validity period, and digital signature. X.509 certificates are used to verify the authenticity and integrity of entities in a networked environment.
- Public Key Infrastructure (PKI): X.509 certificates are typically managed within a PKI, which consists of a set of hardware, software, policies, and procedures used to generate, distribute, manage, and revoke digital certificates. A PKI provides the foundation for secure communication and authentication in various applications, including secure email, web browsing, and virtual private networks (VPNs).
- Certificate Authorities (CAs): CAs are trusted entities responsible for issuing and signing X.509 certificates. They verify the identity of certificate applicants and sign their certificates using the CA’s private key. CAs establish a trust hierarchy through the use of hierarchical or cross-certification models, enabling certificate chains and trust paths to be established.
- Certificate Revocation: X.509 certificates can be revoked before their expiration date if they are compromised, no longer valid, or if the entity’s private key is compromised. Certificate revocation is managed through Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol (OCSP) services. CRLs contain a list of revoked certificates, while OCSP provides real-time verification of the status of a certificate.
- Certificate Validation: Before relying on an X.509 certificate, the recipient needs to validate its authenticity and integrity. This involves verifying the certificate’s signature, checking the certificate’s validity period, and ensuring that the certificate’s chain of trust is valid. The validation process typically involves verifying the digital signature using the CA’s public key and checking the certificate’s validity against the CA’s CRL or OCSP service.
- Secure Socket Layer/Transport Layer Security (SSL/TLS): X.509 certificates are extensively used in SSL/TLS protocols to establish secure communication between clients and servers. During the SSL/TLS handshake process, the server presents its X.509 certificate to the client, which validates the certificate to ensure the server’s identity and establish an encrypted connection.
- Client Authentication: X.509 certificates can also be used for client authentication, where the client presents its certificate to the server to prove its identity. This is commonly used in VPNs, wireless networks, and other environments where strong client authentication is required.
X.509 authentication services play a crucial role in ensuring the authenticity and integrity of entities in networked environments. By leveraging X.509 certificates, entities can establish trust, securely exchange information, and authenticate themselves in various applications and protocols.
What is an X.509 certificate?
An X.509 certificate is a digital certificate that uses the widely accepted international X.509 public key infrastructure (PKI) standard to verify that a public key belongs to the user, computer or service identity contained within the certificate.
A public key is a large numerical value used to encrypt data or check the legitimacy of a digital signature. A PKI, moreover, is the underlying framework that enables entities like users and servers to securely exchange information using digital certificates.
The X.509 certificate is a safeguard against malicious network impersonators. When a certificate is signed by a trusted authority, or is otherwise validated, the device holding the certificate can validate documents. It can also use a public key certificate to secure communications with a second party.
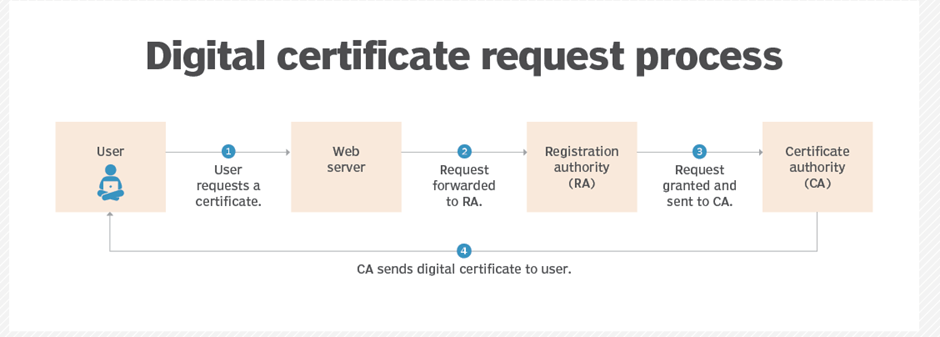
The X.509 certificate is defined by the International Telecommunication Union’s Telecommunication Standardization Sector (ITU-T).
In cryptography, the X.509 certificate securely associates cryptographic key pairs of public and private keys with websites, individuals or organizations. The certificate is typically used to manage identity and security in computer networking and over the internet. For the internet, it is used in numerous protocols to ensure a malicious website doesn’t fool a web browser. The X.509 certificate is also used to secure email, device communications and digital signatures.
The X.509 standard is based on Abstract Syntax Notation One, an interface description language. An X.509 certificate contains an identity and a public key. It binds an identity — such as an individual or hostname — to a public key with a digital signature. The signature is either made by a trusted certificate authority (CA) or is self-signed. Some digital certificates can also be automated.
X.509 certificate fields
An X.509 certificate contains information about the identity to which the certificate is issued and the identity that issued it. Standard information in an X.509 certificate includes the following:
- Version. Which X.509 version applies to the certificate, indicating what data the certificate must include.
- Serial number. The CA creating the certificate must assign it a serial number that distinguishes the CA certificate from other certificates.
- Algorithm information. The signature algorithm the issuer uses to sign the certificate.
- Issuer distinguished name. The name of the entity issuing the certificate — usually, the CA.
- Validity period of the certificate. The start and end date, as well as the time the certificate is valid and can be trusted.
- Subject distinguished name. The name to which the certificate is issued.
- Subject public key information. The public key associated with the identity.
- Extensions (optional). Extensions have their own unique IDs, expressed as a set of values called an object identifier. An extension can be rejected if it is not recognized or if the extension has information that can’t be processed.
Applications of X.509 certificates
Common applications of X.509 certificates include the following:
- Digital identities. A key use of X.509 certificates can be to authenticate the digital identities of devices, people, data and applications.
- TLS/SSL and web browser security. PKI and X.509 are the basis for the Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols. Web browsers read the X.509 certificate of a webpage to verify its TLS/SSL status.
- Digital signatures and document signing. X.509 certificates can authenticate the identity of a digitally signed document, specifically authenticating both the signature and document.
- Email certificates. Secure email standards — for example, Secure/Multipurpose Internet Mail Extensions, or S/MIME — use X.509 certificates.
- Secure Shell keys. Secure Shell (SSH) keys are a form of X.509 certificate. They provide secure access credentials used in the SSH protocol.
- Code signing. Code signing uses certificates to authenticate code so end users can verify that code has not been altered by a third party.
Benefits of X.509 certificates
Potential benefits that come with X.509 certificates include the following:
- Wide area of use. X.509 certificates are a part of web browser security, web server security, online document signing, SSH keys and email security.
- Level of trust. Certificates help safeguard against potentially malicious network impersonators.
- How signed certificates are issued. Certificates are signed by a publicly trusted issuer, such as a CA, or self-signed.
History of X.509 certificates
The first X.509 certificates were issued in 1988 as part of the ITU-T and the X.500 directory services standard. The current version, version 9, was defined in October 2019.
As more versions came out, more certificate fields were added or refined. For example, in 1993, version 2 added two fields to support directory access control, as well as subject and issuer unique identifiers. The X.509 version 3 certificate was released in 1996 and defines the formatting used for certificate extensions. It also was used by the Internet Engineering Task Force in the development of its own X.509 Public Key Infrastructure Certificate and Certificate Revocation List, or CRL, Profile standard.