Secure Hyper Text Transfer Protocol (SHTTP) is an older secure communication protocol that was developed as an extension to the Hypertext Transfer Protocol (HTTP). SHTTP aimed to provide secure transmission of data over the internet by adding encryption and authentication mechanisms to the standard HTTP protocol.
Here are some key points about SHTTP:
- Encryption: SHTTP employs encryption algorithms to protect the confidentiality of data during transmission. It encrypts the data using symmetric key cryptography, ensuring that it cannot be intercepted and understood by unauthorized parties.
- Authentication: SHTTP includes mechanisms for authenticating the identities of the communicating parties. It allows the client and server to verify each other’s identity to prevent impersonation and man-in-the-middle attacks.
- Message Integrity: SHTTP ensures the integrity of the transmitted data by using cryptographic techniques such as message digests or checksums. These techniques verify that the data has not been tampered with during transit.
- Compatibility: SHTTP was designed to be compatible with existing HTTP applications and infrastructure. It aimed to provide security without requiring significant modifications to existing web servers and clients.
- Limitations: Despite its intentions, SHTTP had several limitations that hindered its widespread adoption. One of the main limitations was that it required pre-established secure channels between the client and the server, which made it less flexible for dynamic web environments. Additionally, SHTTP did not address some of the security vulnerabilities present in HTTP, such as session hijacking and cross-site scripting.
It’s important to note that SHTTP is not widely used today. Instead, the industry has transitioned to using the more secure and robust protocols such as HTTPS, which is based on the Secure Sockets Layer (SSL) and its successor, the Transport Layer Security (TLS) protocols. HTTPS has become the standard for secure communication on the web, providing encryption, authentication, and data integrity for websites and web applications.
In summary, while SHTTP was an early attempt at securing HTTP-based communication, it did not gain widespread adoption and has been largely superseded by the more secure and widely supported HTTPS protocol.
Secure Hypertext Transfer Protocol (S-HTTP) is an obsolete alternative to the HTTPS protocol for encrypting web communications carried over the Internet. It was developed by Eric Rescorla and Allan M. Schiffman at EIT in 1994[1] and published in 1999 as RFC 2660.
Even though S-HTTP was first to market,[2] Netscape’s dominance of the browser market led to HTTPS becoming the de facto method for securing web communications.
S-HTTP stands for Secure Hypertext Transfer Protocol, is an Internet protocol for encryption of Hypertext Transfer Protocol (HTTP) traffic. Secure Hypertext Transfer Protocol (S-HTTP) is an application-level protocol that extends the HTTP protocol by adding encryption to Web pages. It also provides mechanisms for authentication and signatures of messages.
S-HTTP provides broad support for implementing different types of cryptographic algorithms and key management systems. Although S-HTTP systems can make use of digital certificates and public keys, messages can also be encrypted on a per-transaction basis using symmetric session keys. S-HTTP was proposed as a draft standard in 1996 and is still under development.
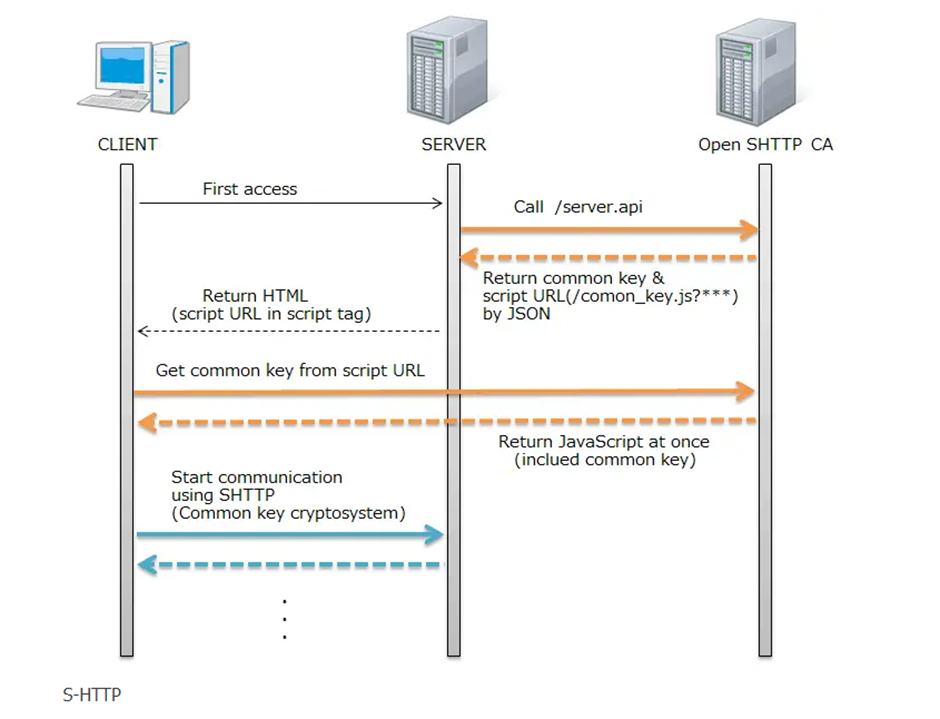
S-HTTP is also a server software
S-HTTP is not as widely implemented as Secure Sockets Layer (SSL), which is independent of protocol and works with HTTP, Simple Mail Transfer Protocol (SMTP), Network News Transfer Protocol (NNTP), and other Internet protocols.
S-HTTP is also the name given to World Wide Web (WWW) server software that implements the S-HTTP protocol. This software was developed by Enterprise Integrations Technologies (EIT), the National Center for Supercomputing Applications (NCSA), and RSA Security.
